Last Friday I was finishing my first hackathon with Techfugees and Diginauts in Copenhagen. Such events are really good for meeting people with similar values and motivations but coming from different backgrounds. That diversity generally brings awesome results. I will present to you the work we’ve done after 48 hours of work.
The project: Pasarán
To directly jump on the project we worked on, and technology oblige for a hackathon, I present you the app Pasarán. Its goal is to help people documenting their journey while crossing borders to save proofs in case of a pushback.

The speech
1. Introduction
In July 2019, a Croatian police officer sent a letter to the local Ombudsman stating that he performed pushbacks at the border on more than 1000 people. This whistleblower brings a well known but poorly documented topic: pushbacks within the EU and its borders.
A pushback is literally when someone who just crossed a border is being forced to return, and therefore is denied of they right to apply for asylum. The legal term, more broad, is refoulement.
It’s illegal.

To bring back some context, the last two months more than 20000 persons crossed the Greek border to get in the EU (source). That’s 358 persons a day.
PS: We won’t give global Mediterranean numbers as so many people died in Central Med without us knowing about, that the statistic would be way too far away from the truth.
On the other side, and within the same timeframe, more than 500 people got illegally pushback in the Balkan region (source)… and that’s only for the few we know thanks to the work of Borderviolence.eu.
It means that right now, while you’re reading these lines, this violence may be happening in the EU.
2. Pasarán: what is it?
Pasarán will do its best to help the people victim of human rights abuses at the borders by collecting evidence in a secure and encrypted way.
We came with one idea: the data collected from one individual’s phone will be encrypted and sent to a unique chosen trustee like a family member or a close friend. Once the journey is completed and depending on the issue, the person chooses to keep or erase the encrypted file.
2. How does it work? Introduction
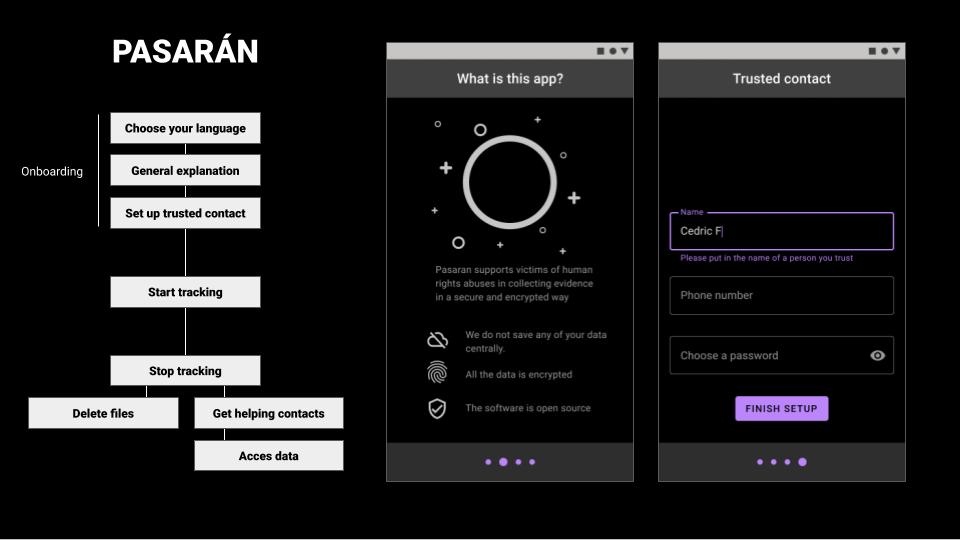
The process works like this:
– A four slides onboarding helps to choose a language, describes what is the app about, how to use it, and explains important notions such as data-privacy and legal rights of the user.
– The person is invited to write the phone number of one trustee and create a password.
– The trustee receives an invitation to download the app and is invited to send a confirmation back directly from the app (public key get exchanged at the same time).
3. How does it work? The D day

– When the important day arrives, the person turns on the app. It shows a simple black interface with only vital info to reduce the battery’s consumption. A first location is sent. Note that no other coordinates will be sent until the border is crossed or the emergency button is pressed to avoid memorizing a precise traveling path.
4. How does it work? The border
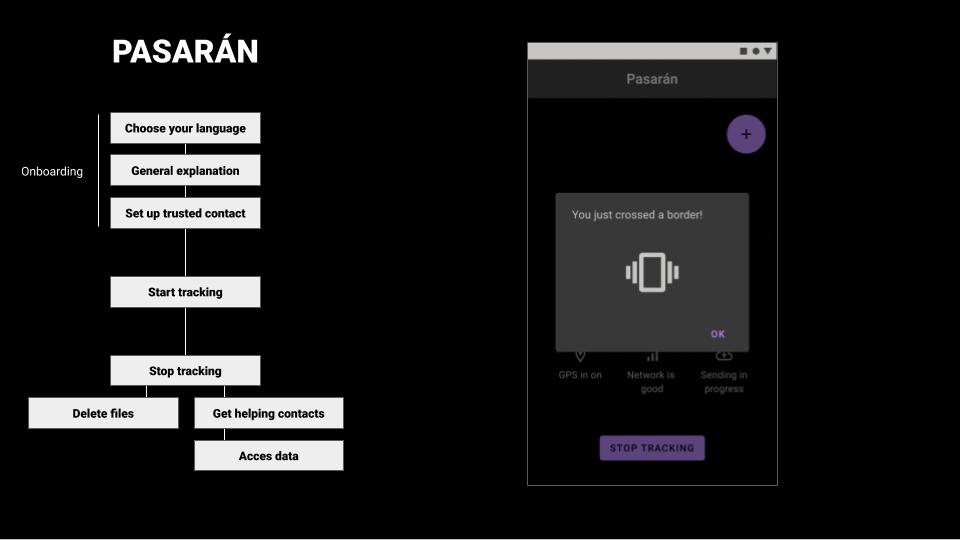
– Once the border is crossed the phone vibrates to inform the user. A location and timestamp is sent to the trustee and can be used later as proof that the person crossed the border.
– If the area seems safe, it’s time to collect evidence: a bus stop, a bar, a car, a river, … Lawyers told us photos are good proof that someone was in a country, therefore, we implemented a shortcut to access the camera. Everything is immediately encrypted and transferred to the trustee.
– It’s advised during the training to NOT use the phone in case of pushback to avoid physical violence from the “refoulers” therefore we implemented an emergency button. In case of fear of pushback, the user can triple-tap the sound button of they phone which will activate in the background the audio recording and send a last-known location to the trustee. The phone should stay in the pocket during this operation.
5. How does it work? After

– Once the travel is done and depending on the outcome, the person can choose to keep the data or erase the data. The user can download the encrypted file and access all the evidence by using the unique password.
– Depending on the issue, the app might redirect the users to competent actors that will advise them on the legal procedure or following steps.
6. Conclusion

I prepared an article about the hackathon itself and how to get ready as a designer, stay tuned!

